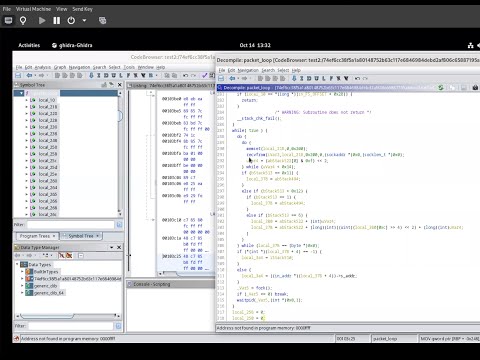
Скачать клипы Tracing and Detecting Malware using eBPF ↓

LinuxDays 2019 - Inspect IoT malware: Intro to Linux tracing and behavioral analysis- Daniel Uhříček

Analysis of offensive capabilities of eBPF and implementation of a rootkit-Marcos Bajo Juan Tapiador