Скачать клипы Piloting Around the Rocks: Avoiding Threats in Kubernetes ↓

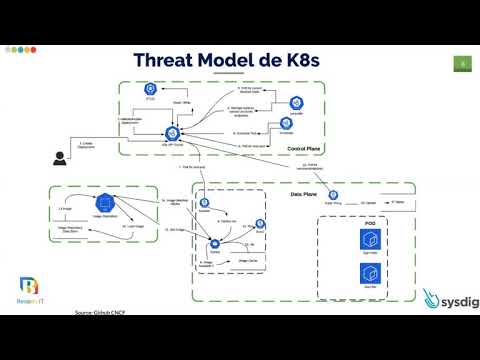
Know Your Enemy: Mapping Security Risks Using Threat Matrix for Kuber... Yossi Weizman & Ram Pliskin

Knock Knock: Security threats with Kubernetes (Ukr version) - Igor Khoroshchenko, Stanislav Kolenkin