Скачать клипы OffensiveCon23 ↓

OffensiveCon23 - Dave Aitel - Information Security Is an Ecology of Horrors and You Are the Solution
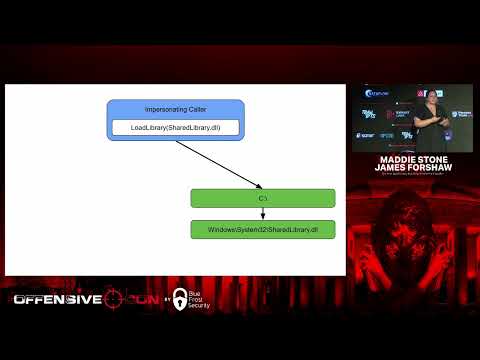
OffensiveCon23- Maddie Stone & James Forshaw- The Print Spooler Bug that Wasn’t in the Print Spooler

OffensiveCon23 - Dave Aitel - Information Security Is an Ecology of Horrors and You Are the Solution

OffensiveCon23- Maddie Stone & James Forshaw- The Print Spooler Bug that Wasn’t in the Print Spooler